as of today I noticed I can’t access my plex server at all when on my work’s wifi. But if i swtich to 4g i can watch plex just fine. But obviously mobile data isn’t truly unlimited high speed. And yes I only watch shit on my break. I have remote access enabled etc. Not sure what I can do?
VPN to your home network (wg-easy is the easiest way to set this up) or change the public port of your server to something the work network will allow.
Use a vpn. Cloudflare warp isn’t officially a vpn iirc, but it does unblock any site.
If they block plex, they probably block private vpns as well (or if they don’t you’d most likely be violating some policy). So other than politely asking your IT admin to unblock it, there’s exactly nothing you can do.
You don’t. Jesus Christ. It’s their network.
Step outside, touch grass and use the cell signal.
Get a better catchphrase, “touch grass” is so overused now it’s embarrassing.
Go outside and punch a tree!
Great, now I’m out of touch and my hand hurts.
I came here to touch trees and smoke bubblegum … and I’m all out of touch.
I’m out of touch and want to play Minecraft!
Get fucked. Better?
Hey, let’s be civil.
Lol okay neckbeard
I simply changed my public port to 443 in Plex and made a port forward on my home router. 443 -> internal_ip:32400
How do I do this?
On your Plex server, you change the public port here
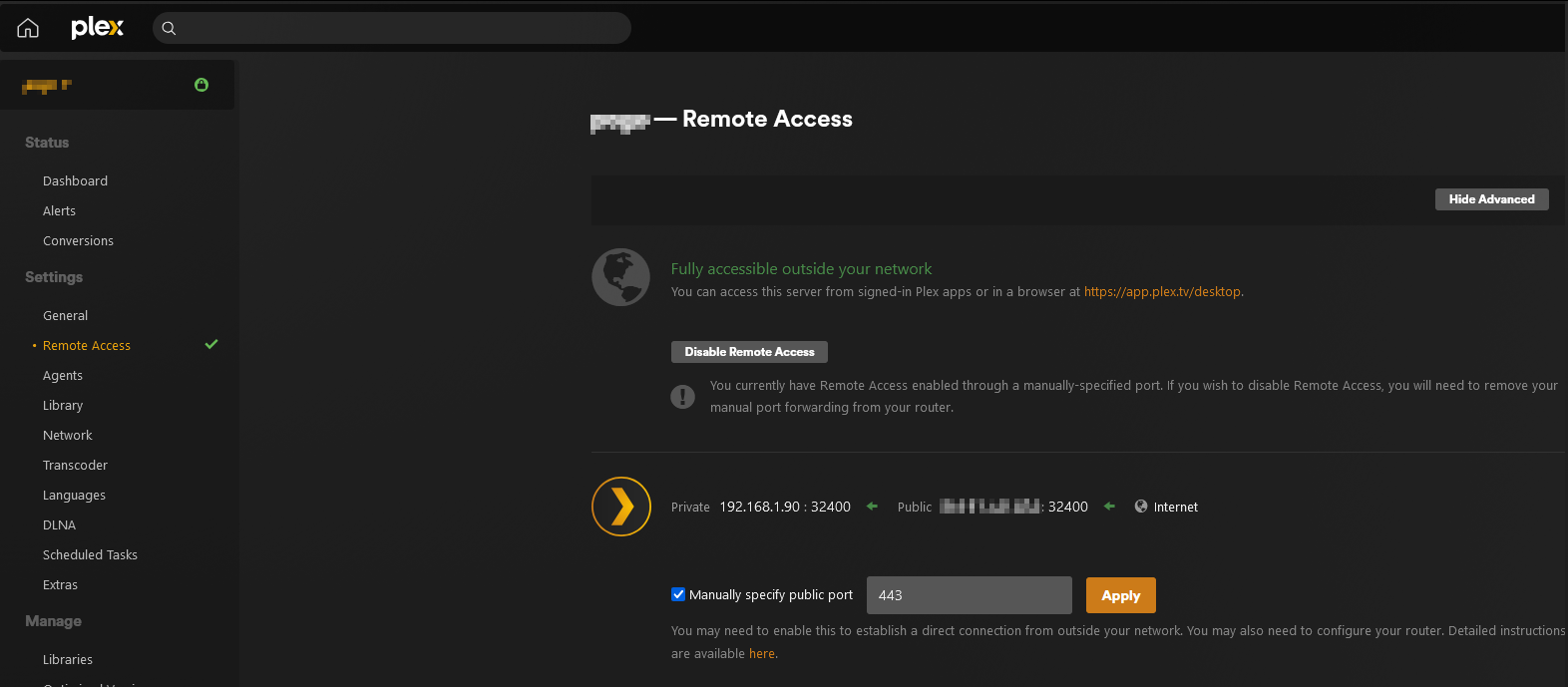
On your home router, you reserve the IP address (aka DHCP reservation) assigned to the machine hosting the Plex server (or you assign a static IP address to it) in my case it’s
192.168.1.90, then you make a port forward so that port 443 on your public address is forwarded to your internal_ip port 32400.Now the home router part is specific to your router brand and model, so you’ll have to do some research on your end.
I have spectrum so I have the default modem/router they provide which for my use case is just fine. In the spectrum app I can assign port forwards.
Don’t, unless you don’t mind losing your job. They did it because they noticed people were watching stuff at work and they don’t want you to do it.
We don’t know their situation. Might be fine, and they just blocked most ports rather than specifically Plex’s. OP also said they only watch stuff on their break.
Fair enough, that could be the case. Some generic blocking setting. In that case others in this thread have given good technical suggestions.
How about you do your work instead?
This doesn’t answer my question , next!
Well, I do truly hope you get caught in the act.
This doesn’t answer my question, next!
How about you mind your own fucking business? Maybe they watch something on their break?
Ask the IT guy about it.
This is the best idea. Just talk to them, best case they’ll help you with it, worst case is they’ll give you a talking to. Going around IT’s back is a very good way to get fired really quickly.
Bribe them with snacks. Source: Am IT. Have been bribed with snacks. You can bet that user got priority treatment from that day on.
If you’re watching consecutive episodes of a series you can always just download them to your phone before you head to work. Not really viable if you hop around a lot, though.
They might not be blocking plex, but blocking most ports that aren’t relevant to “normal” internet usage. E.g. just have ports 443, 80 and 8080 allowed.
You might have to steer a VPN through those ports too?
Do that shit on your phone. I never understand how many people openly fuck around on company networks. 90% chance they’re logging everything you’re doing.
Download some stuff to your phone/tablet for “offline” viewing. Your work has decided to restrict you from doing non-work stuff on their network and that’s their right.
I think this is only allowed with plexpass but I’m not positive.
i should mention i have lifetime plexpass
Then this is definitely your easiest and safest way to go: no new services to configure, no rolling the dice to see how upset the org will be about possible policy violations.
Wow, $120 to be able to download your own shit… I’m glad I chose jellyfin.
I paid $80 one time years ago
Fair enough, it probably made sense at the time. Still, disappointing from Plex.
It was the only game in town for ages, and the one-time payment thing for a lifetime pass was taken advantage of by a ton of people, including myself.
Inb4 they drop support for “lifetime” in a couple of years and tell you to pay for a monthly subscription
Correct
VPN to LAN, great for remote access of other things on your home LAN as well. Once connected it will be as if your phone was on your home WiFi.
So I have Windscribe as my VPN, what do I do exactly?
That’s not “Windscribe as my VPN”, it’s a VPN to Windscribe’s servers.
You want to setup a VPN to your home network. This is one option: https://tailscale.com/
ooo, this looks very nice. I shall try setting this up, thanks
This is the answer.
This is the answer…
… to get him fired.
Forgive my ignorance, but how would they know? Wouldn’t they just see a VPN connection and where it’s going, but not what’s happening across the VPN?
I’m just glad I don’t have to deal with this. Even if I use the WiFi at work, it’s for public use and there’s no restriction with regards to streaming.
They’d see a VPN connection, where it’s going, how much traffic it’s using, and the origination point on the network. Might as well put up a giant red arrow over your desk.
Don’t do this. This is going to trip alarms on any half decent IDS, and your net admins are busy enough without having to write up a report to go to the HR people deciding if they are going to fire you for breaking the computer use policy
Using a VPN on wifi shouldn’t trip anything.
Whose WiFi? The companies WiFi? Why would that be any different to the wired network?
If you’re letting random mobile devices on the internal network, you’ve already failed security 101.
deleted by creator
Exactly! And you shouldn’t care if someone fires up a VPN on a guest network! I would expect them to actually.
It honestly depends on the network policies you’re dealing with. Some employers have strict security and won’t allow workarounds like vpns or proxies, and they really don’t want you connecting the network to other unsecured ones.
That said, I’d try a personal VPN (not necessarily a proxy one, just one that can connect you to your plex server on a shared network). If that doesn’t work, I really doubt it’s a good idea to connect to your plex server from their wifi anyway. If that’s the case, I would just download the media I want before I get to work
Try setting up tailscale














